In today’s digital landscape, user experience (UX) reigns supreme. This is especially true within the enterprise software realm, where SAP continues to innovate with its intuitive SAP Fiori interface. But exceptional UX goes hand-in-hand with robust security. So, how does SAP Fiori ensure secure access to critical business data? This blog dives deep into the world of SAP Fiori security, unpacking its core principles and best practices.
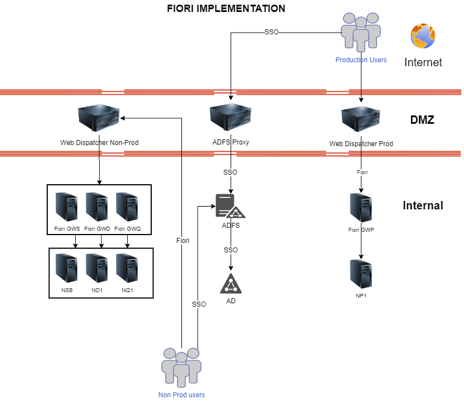
Understanding What is SAP Fiori Security: A User-Centric Approach
SAP Fiori represents a significant shift from traditional SAP interfaces. It offers a modern, consumer-grade experience, featuring intuitive design elements and role-based app functionality. Users can access relevant applications through a central launchpad, streamlining workflows and boosting productivity.
The Security Foundation of SAP Fiori
Here’s what underpins the secure environment within SAP Fiori:
- Authorization Controls: Access to SAP Fiori apps and data is governed by a layered authorization system. This system leverages pre-defined business roles, which dictate the specific actions and information a user can access.
- Single Sign-On (SSO): Users authenticate once to gain access to the entire SAP Fiori launchpad and its associated apps. This eliminates the need for multiple logins, enhancing convenience and security.
- Data Security: SAP Fiori applications inherit the robust security protocols of the underlying SAP system. Data encryption, access controls, and user activity audits ensure information remains protected.
- Secure Communication: Communication between the SAP Fiori launchpad, applications, and back-end systems leverages secure protocols like HTTPS, safeguarding data transmission.
Core Principles of SAP Fiori Security
- Least Privilege: Users are granted only the minimum level of access required to perform their tasks. This minimizes the potential damage caused by unauthorized access.
- Separation of Duties (SoD): Critical tasks are divided among different users, reducing the risk of fraud or manipulation.
- Regular Reviews and Audits: Security configurations and user permissions are periodically reviewed and audited to identify and address any vulnerabilities.
Best Practices for Enhanced Security
- Maintain Strong Passwords: Enforce complex password policies and encourage regular password changes for all users.
- Implement Multi-Factor Authentication (MFA): Add an extra layer of security by requiring a secondary verification factor, such as a code from a mobile authenticator app.
- Minimize User Privileges: Assign roles and permissions judiciously, granting only the specific access needed for a user’s job function.
- Stay Updated: Regularly apply security patches and updates to the SAP Fiori system and underlying infrastructure to address newly discovered vulnerabilities.
- Educate Users: Train users on security best practices, including password hygiene, suspicious activity reporting, and phishing email awareness.
Why Does SAP Fiori Security Matter?
Robust security in SAP Fiori is paramount for several reasons:
- Protects Sensitive Data: Businesses entrust SAP with critical financial information, customer data, and intellectual property. Secure access controls prevent unauthorized individuals from compromising this sensitive data.
- Maintains Regulatory Compliance: Many industries have strict data privacy regulations. Robust Fiori security helps ensure compliance with these regulations, avoiding hefty fines and reputational damage.
- Minimizes Business Disruption: Security breaches can lead to system downtime, data loss, and operational disruptions. Effective Fiori security safeguards businesses from these costly consequences.
Conclusion
By understanding the core principles and best practices of SAP Fiori security, organizations can leverage the full potential of this user-centric interface while maintaining the highest levels of data protection. By implementing a layered security approach, businesses can empower users with a seamless work experience while mitigating security risks.