Introduction
Overseeing Weaknesses in Custom SAP Code and Outsider Combinations As organizations keep on digitizing their tasks and influence ERP frameworks, SAP has turned into a basic piece of their foundation. SAP, with its hearty set-up of programming, works with big business asset arranging, assisting organizations with overseeing processes across different divisions like money, obtainment, and HR. Notwithstanding, as SAP turns out to be more implanted in the functional texture of associations, it likewise presents a large group of safety challenges, especially with regards to custom SAP code and outsider reconciliations. SAP frameworks frequently require custom code and outsider incorporations to meet explicit business needs, yet these customizations can incidentally present weaknesses. Dealing with these weaknesses is pivotal to keeping up with the security, honesty, and execution of the SAP scene. This blog will investigate the difficulties related with overseeing weaknesses in custom SAP code and outsider mixes and deal best practices to alleviate possible dangers.
1. Understanding Vulnerabilities in Custom SAP Code and Third-Party Integrations
1.1 What Are Custom SAP Code Vulnerabilities?
SAP conditions are frequently modified to fit explicit business necessities. These customizations incorporate making new projects, altering standard SAP applications, or growing new functionalities. While customization is fundamental for addressing business needs, it can present weaknesses that compromise the framework’s security.
Weaknesses in custom SAP code commonly originate from:
- Poorly Written Code: Custom code that is wasteful, inappropriately organized, or not completely tried may contain security blemishes, for example, infusion weaknesses or unfortunate mistake dealing with, making it simpler for assailants to take advantage of.
- Inadequate Input Validation: Quite possibly of the most widely recognized weakness in custom SAP code is neglecting to appropriately approve input from outside sources, which can prompt SQL infusion or cross-site prearranging (XSS) assaults.
- Hardcoded Credentials: Engineers here and there hardcode accreditations, for example, usernames, passwords, or Programming interface keys into custom SAP programs. These qualifications, whenever uncovered, can be effortlessly taken advantage of by aggressors.
1.2 Vulnerabilities in Third-Party Integrations
SAP frequently coordinates with outsider instruments and frameworks to extend usefulness, upgrade client experience, and smooth out business tasks. Be that as it may, these outsider incorporations can present weaknesses in the event that not oversaw cautiously.
Outsider joining weaknesses might include:
- Insecure APIs: Ineffectively executed APIs can uncover delicate information and framework usefulness to unapproved parties. Assuming the Programming interface needs appropriate verification, encryption, or information approval, assailants might acquire unapproved access.
- Supply Chain Attacks: Assailants might take advantage of shortcomings in the outsider merchant’s framework, permitting them to think twice about associated SAP framework. These assaults can spread undetected through programming refreshes or unreliable associations.
- Unpatched Vulnerabilities in Third-Party Software: While coordinating outsider applications, associations frequently depend on merchants to keep their frameworks refreshed. Assuming that the merchant neglects to fix known weaknesses, the coordination might be in danger of abuse.
2. Best Practices for Managing Vulnerabilities in Custom SAP Code
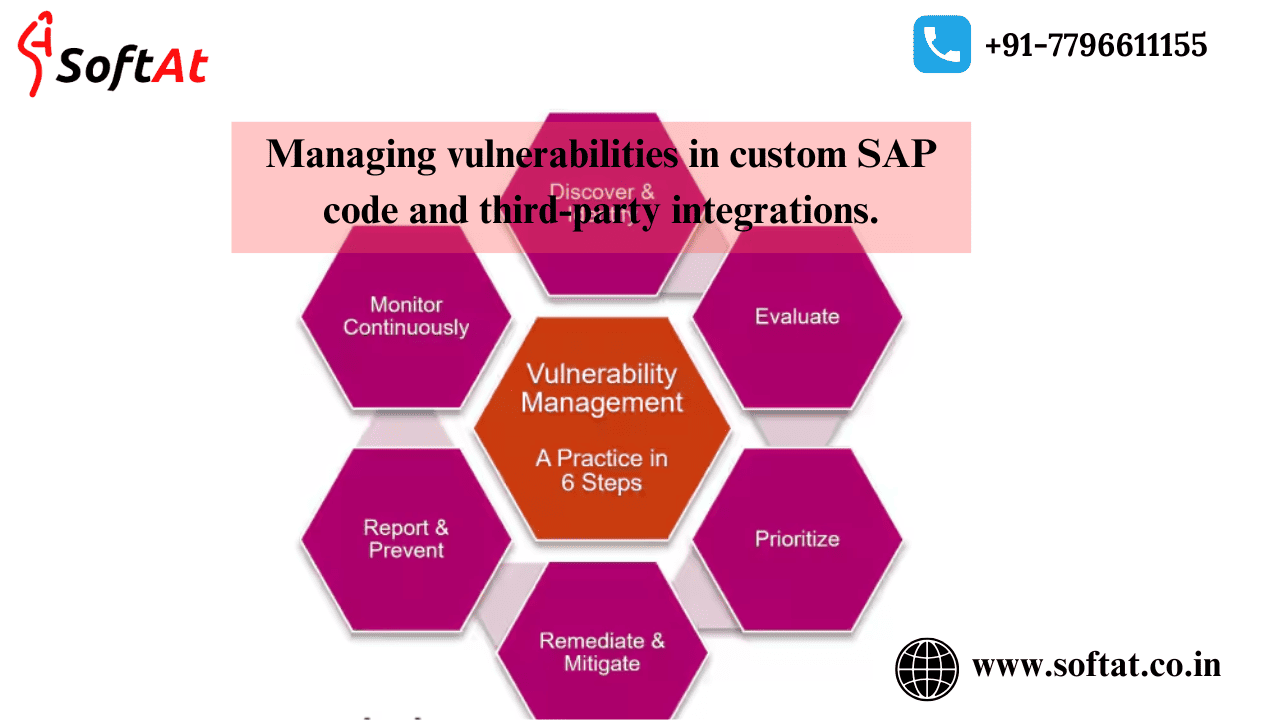
To guarantee the security of custom SAP code, associations should take on accepted procedures that attention on secure turn of events, testing, and continuous upkeep. Here are a few vital practices to follow:
2.1 Conduct Secure Coding Practices
Secure coding is the groundwork of relieving weaknesses in custom SAP code. Engineers ought to observe industry guidelines for secure coding, like the OWASP (Open Web Application Security Venture) rules. These incorporate practices like:
Input Validation: Consistently approve and disinfect input from all client sources of info and outer frameworks to forestall SQL infusion and XSS assaults.
Error Handling: Execute powerful blunder dealing with systems that don’t uncover touchy data in blunder messages. Definite blunder data ought to never be presented to end-clients.
Use of Parameterized Queries: To keep away from SQL infusion assaults, consistently use defined inquiries or arranged explanations while cooperating with information bases.
Avoid Hardcoding Credentials: Never hardcode delicate information, for example, passwords or Programming interface keys into the code. Utilize secure strategies to oversee certifications, for example, SAP’s Protected Stockpiling or outsider arrangements like Vault.
2.2 Regular Code Reviews and Static Code Analysis
- Normal code surveys and robotized static code examination are fundamental for distinguishing weaknesses right off the bat in the improvement lifecycle. Code surveys permit experienced designers to distinguish potential security chances, for example, unreliable information dealing with or defective confirmation instruments, before the code is sent.
- Static code examination instruments, like SonarQube or SAP Code Reviewer, can check the custom code for normal weaknesses and assist with authorizing coding principles. These devices can identify issues like unvalidated input, hardcoded certifications, and other normal security imperfections, which can be rectified before they become an issue.
2.3 Implement Strong Authentication and Authorization Controls
While creating custom SAP applications, it is vital to execute solid verification and approval controls. Use job based admittance control (RBAC) to guarantee that main approved clients approach explicit capabilities inside the framework. Moreover:
- Multifaceted Verification (MFA) ought to be utilized any place conceivable to add an additional layer of safety.
SAP’s Security Review Log can be empowered to follow unapproved access endeavors and recognize potential security breaks. - These controls assist with restricting the harm in case of a break by guaranteeing that aggressors can’t raise their honors.
2.4 Regular Patch Management and Updates
- Custom SAP code should be kept up with and refreshed consistently to guarantee it stays secure. Designers ought to remain informed about SAP’s security patches and any weaknesses recognized in the SAP security fix day. Assuming custom code depends on unambiguous SAP parts, it’s vital to guarantee that these parts are constantly fixed to the most recent adaptation.
- Staying up with the latest with security patches lessens the gamble of abuse of known weaknesses. A legitimate fix the executives technique ought to be carried out to guarantee opportune updates across the whole SAP scene.
3. Best Practices for Managing Vulnerabilities in Third-Party Integrations
Outsider mixes can present huge dangers while perhaps not appropriately made due. The following are best practices for overseeing weaknesses in outsider combinations with SAP:
3.1 Assess the Security Posture of Third-Party Vendors
Prior to coordinating outsider applications or administrations with SAP, it is essential to assess the security stance of the seller. This incorporates:
- Security Certifications: Confirm that the outsider seller adheres to industry guidelines for security, for example, ISO 27001 or SOC 2.
- Penetration Testing: Guarantee that outsider applications have gone through ordinary security testing, including infiltration tests to recognize weaknesses.
- Incident Response Plan: Guarantee that the seller has a clear cut occurrence reaction plan set up in the event of a security break.
3.2 Secure API Connections
APIs are the essential strategy for incorporating outsider administrations with SAP. To get these associations, associations ought to:
- Use Secure Communication Protocols: Consistently use TLS (Transport Layer Security) to scramble information sent between frameworks. Never depend on decoded associations for APIs.
- Implement API Authentication: Use OAuth, Programming interface keys, or endorsements to validate Programming interface calls and guarantee just approved frameworks can collaborate with SAP.
- Rate Limiting: Implement rate limiting and IP whitelisting to prevent abuse and DDoS attacks on the APIs.
3.3 Perform Regular Vulnerability Scanning and Monitoring
- To distinguish possible weaknesses in outsider combinations, perform normal weakness filters. Devices, for example, Qualys or Nessus can check the SAP climate and any outsider reconciliations for known weaknesses.
- Moreover, consistent checking apparatuses like SAP Arrangement Supervisor or SIEM (Security Data and Occasion The executives) arrangements can assist with following dubious exercises and identify oddities in the framework. This proactive methodology guarantees that any potential weaknesses are tended to before they can be taken advantage of.
3.4 Control Data Sharing and Minimization
To diminish the assault surface, try not to over-impart delicate information to outsider applications. Carry out the rule of least honor by guaranteeing that outsider combinations just approach the information important for their particular capability. Furthermore:
- Data Masking: Use information covering methods to muddle delicate data, for example, Visa subtleties or individual recognizable proof information, while offering it to outsider sellers.
- Contractual Agreements: Guarantee that all outsider combinations are covered by security-centered arrangements, including statements around information security, occurrence detailing, and obligations in the event of a break.
4. Conclusion
- Overseeing weaknesses in custom SAP code and outsider mixes is a continuous test, yet it is essential to the general security of a SAP framework. By following prescribed procedures, for example, secure coding, leading code surveys, utilizing hearty verification systems, and getting outsider mixes, organizations can relieve the dangers related with weaknesses in SAP scenes.
- Security is certainly not a one-time fix; it requires consistent carefulness and proactive administration. Ordinary updates, constant checking, and continuous correspondence with outsider merchants are critical to keeping a solid SAP climate. By taking a far reaching, diverse way to deal with weakness the board, associations can shield their SAP framework against developing digital dangers and keep up with the respectability of their basic business processes.
You may be interested in:
A Deep Dive into SAP API Management
Integration cloud system to HANA Cloud Platform using Cloud Connector