Introduction
In an undeniably computerized world, digital dangers have become more refined, successive, and harming. As associations rely more upon innovation and cloud-based administrations, the gamble of cyberattacks develops dramatically. Conventional safety efforts, like firewalls and antivirus programming, frequently miss the mark with regards to safeguarding against the high level, exceptionally designated assaults of today. To counter these dangers, organizations are going to cutting edge danger location and reaction frameworks (ATDRS) that influence state of the art advancements, for example, AI (ML), man-made reasoning (man-made intelligence), and robotization to recognize, dissect, and alleviate digital dangers progressively.
1. Understanding Advanced Threat Detection and Response Systems
1.1 What Are Advanced Threat Detection and Response Systems?
- High level Danger Identification and Reaction (ATDR) frameworks are a developed type of customary security apparatuses, intended to distinguish and relieve the most complex digital dangers. These frameworks depend on a mix of AI, social examination, and computerized reaction capacities to recognize and answer noxious exercises continuously.
- Not at all like ordinary security devices that fundamentally center around known dangers, ATDR frameworks are intended to perceive both known and obscure assaults. By consistently checking network traffic, client conduct, endpoints, and applications, they can distinguish uncommon or dubious movement that could show a possible danger. When a danger is identified, the framework naturally answers by secluding the impacted framework, impeding malevolent traffic, or cautioning security groups for additional examination.
1.2 The Evolution of Cyber Threats
- Digital dangers have advanced emphatically throughout the course of recent many years. Aggressors never again depend entirely on conventional methods, for example, malware or phishing assaults. Today, cybercriminals utilize many high level strategies, including zero-day takes advantage of, cutting edge steady dangers (APTs), and ransomware.
- Zero-Day Exploits: These are assaults that target weaknesses in programming or equipment before the designer gets an opportunity to deliver a fix. Recognizing zero-day takes advantage of requires frameworks that can distinguish unusual way of behaving as opposed to depending on known danger marks.
- Advanced Persistent Threats (APTs): APTs are long haul, designated assaults intended to acquire unapproved admittance to frameworks over a lengthy period. These assaults are normally done by all around financed and talented cybercriminals or country state entertainers.
- Ransomware: Ransomware assaults are turning out to be progressively complex, with assailants focusing on basic frameworks and requesting installment in return for reestablishing admittance to information. Identification of such goes after in their beginning phases is vital to limiting harm.
2. Key Components of Advanced Threat Detection and Response Systems
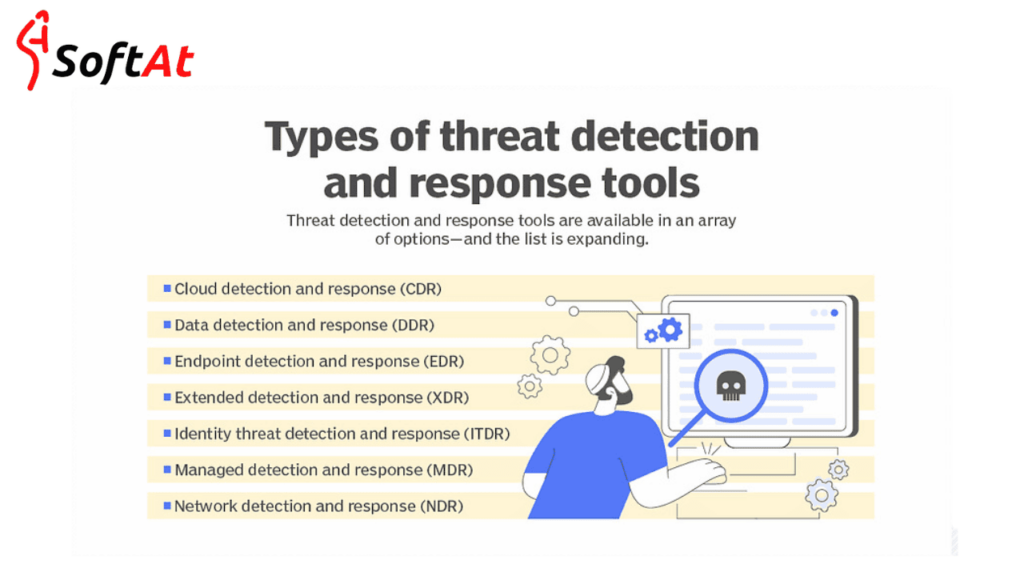
- High level danger discovery and reaction frameworks consolidate a few innovations and philosophies to give exhaustive security against current digital dangers. The following are a portion of the vital parts of ATDR frameworks:
2.1. Machine Learning and AI
- AI and man-made brainpower are at the center of present day ATDR frameworks. These advances empower the framework to ceaselessly gain from new information, adjust to developing dangers, and distinguish oddities continuously.
- Anomaly Detection: AI calculations can be utilized to investigate network traffic and client ways of behaving to recognize deviations from the standard. These deviations could show a potential digital danger.
- Predictive Capabilities: artificial intelligence fueled frameworks can anticipate potential weaknesses in light of verifiable information and known assault vectors. By distinguishing shortcomings before they are taken advantage of, associations can fortify their safeguards proactively.
2.2. Behavioral Analytics
- Conduct examination is a procedure used to screen and dissect the activities of clients and frameworks. By laying out a standard of ordinary way of behaving, an ATDR framework can identify deviations from this benchmark that might show malevolent action. For example, in the event that a client unexpectedly gets to a lot of delicate information beyond their ordinary extent of work, the framework can hail this action as dubious.
- User and Entity Behavior Analytics (UEBA): This is a subset of social examination that spotlights on distinguishing oddities in client or element conduct. It is especially valuable for recognizing insider dangers or compromised accounts, where assailants might mimic authentic clients.
2.3. Threat Intelligence
- Danger insight alludes to the assortment and examination of data about current or arising digital dangers. This information can incorporate danger pointers, for example, IP addresses, area names, and document hashes related with vindictive action.
- High level danger identification frameworks incorporate danger knowledge feeds to improve recognition abilities. By joining outer knowledge with interior checking, these frameworks can distinguish known dangers and immediately perceive new dangers as they arise.
2.4. Automated Response and Orchestration
- When a danger is recognized, an ATDR framework should answer rapidly to forestall further harm. Mechanized reaction capacities are pivotal for limiting the effect of cyberattacks, particularly when security groups are overpowered or inaccessible.
- Automation: The framework can naturally make predefined moves, for example, disconnecting tainted gadgets, obstructing malevolent IP addresses, or crippling compromised accounts. This diminishes the reaction time and restricts the potential harm brought about by an assault.
- Orchestration: ATDR frameworks can incorporate with other security apparatuses like firewalls, SIEM (Security Data and Occasion The board), and Take off (Security Arrangement, Mechanization, and Reaction) stages. This empowers an organized and brought together reaction across various security layers
2.5. Endpoint Detection and Response (EDR)
- Endpoints are many times the essential passage focuses for cyberattacks. Endpoint Identification and Reaction (EDR) arrangements give constant checking and location on gadgets like PCs, work areas, cell phones, and servers.
- An EDR framework inside an ATDR structure can identify dubious conduct on endpoints, break down the danger, and make a move to contain the assault. This is fundamental for moderating the effect of dangers like ransomware or malware that target individual gadgets prior to spreading to the more extensive organization.
3. Benefits of Advanced Threat Detection and Response Systems
- Associations that carry out cutting edge danger discovery and reaction frameworks can receive different rewards. These frameworks give further developed security as well as more prominent functional proficiency and cost-viability in the long haul.
3.1. Faster Detection and Response
- High level ATDR frameworks decisively lessen the time it takes to distinguish and answer dangers. Conventional security frameworks might require human mediation to explore and follow up on a danger, however with computerized reactions and simulated intelligence fueled examination, ATDR frameworks can distinguish and contain dangers progressively.
- Example: A financial establishment utilizing an ATDR framework with AI capacities can rapidly distinguish strange exchanges, like an unexpected withdrawal of enormous totals from numerous records. The framework can naturally hail the exchange, alarming the security group and possibly freezing the exchange before it finishes.
3.2. Reduced Risk of Data Breaches
- One of the most destroying outcomes of a cyberattack is the break of touchy information. ATDR frameworks limit the gamble of breaks by rapidly recognizing noxious exercises, like unapproved admittance to data sets or exfiltration of delicate records, and shutting down these activities before they can raise.
- Example: An internet business organization coordinates UEBA into its ATDR framework, permitting it to distinguish when a representative gets to client installment data beyond their work scope. The framework can set off a caution or lockdown the record to forestall information burglary.
3.3. Improved Resource Efficiency
- Via robotizing the discovery, examination, and reaction to dangers, ATDR frameworks let loose important assets for additional essential errands. Security groups are not generally troubled with consistent observing and manual danger hunting, permitting them to zero in on high-need assignments.
- Example: A medical services association utilizes an ATDR framework that computerizes the location of ransomware on its organization. Rather than having staff continually screen logs, the framework naturally answers, opening up the group to zero in on other significant security drives.
3.4. Scalability and Adaptability
- As associations develop and advance, their security needs change. ATDR frameworks are intended to scale with an association’s foundation, permitting them to deal with a rising volume of information and organization traffic without settling for less on execution. Moreover, these frameworks can rapidly adjust to new and arising dangers, guaranteeing that the association’s security pose stays hearty over the long run.
4. Best Practices for Implementing Advanced Threat Detection and Response Systems
To augment the adequacy of ATDR frameworks, associations should follow specific prescribed procedures:
4.1. Integrate with Existing Security Infrastructure
- Guarantee that your ATDR framework incorporates consistently with existing security devices like SIEM, firewalls, and weakness scanners. Incorporation upgrades perceivability and guarantees that all security layers cooperate durably.
4.2. Regularly Update Threat Intelligence Feeds
- Danger knowledge is dynamic, with new dangers arising everyday. Guarantee that your ATDR framework is ceaselessly refreshed with the most recent danger insight feeds to remain in front of developing assault strategies.
4.3. Conduct Regular Security Training
- ATDR frameworks are strong, yet human mistake stays quite possibly of the most fragile connection in security. Customary security preparing and mindfulness programs are fundamental to guarantee that representatives comprehend how to detect phishing messages, keep away from hazardous ways of behaving, and perceive the indications of a potential cyberattack.
4.4. Monitor and Analyze Security Metrics
- Lay out a bunch of key execution markers (KPIs) to screen the viability of your ATDR framework. Measurements like interim to location (MTTD), mean chance to answer (MTTR), and misleading positive rates can assist with surveying the framework’s exhibition and recognize regions for development.
5. Conclusion
- As digital dangers become more perplexing and challenging to identify, high level danger recognition and reaction frameworks are fundamental for associations hoping to protect their resources and information. By incorporating AI, man-made intelligence, social investigation, and mechanization, ATDR frameworks offer ongoing discovery, quick reaction, and diminished chance of information breaks, all while working on functional proficiency.
- To completely understand the advantages of these frameworks, associations should follow best practices, for example, coordinating with existing security foundation, refreshing danger knowledge takes care of routinely, and leading consistent preparation for staff. The interest in a high level danger identification and reaction framework safeguards against present day dangers as well as fortifies the general security act, permitting organizations to work with trust in the present progressively advanced scene.
You may be interested in:
A Deep Dive into SAP API Management
Integration cloud system to HANA Cloud Platform using Cloud Connector